1.下载 app
2.frida 调试
3.抓包查看接口
4.分析加密数据
5.易语言编写代码
1 .开始下载
下载好发现有越狱检测,检测点为:
-[AppDelegate isJailBreak];于是编写插件xm代码 :
%hook AppDelegate
- (void)isJailBreak{
NSLog(@"AppDelegate isJailBreak method : %@", self);
}
%end编译代码放入:
/Library/MobileSubstrate/DynamicLibraries从新打开 app,即可正常打开了
2.开始frida 调试
经过反复分析,发现关键点为:
GMSm2Utilss
GMSm3Utilss
GMSm4Utilss
直接使用通配符 hook
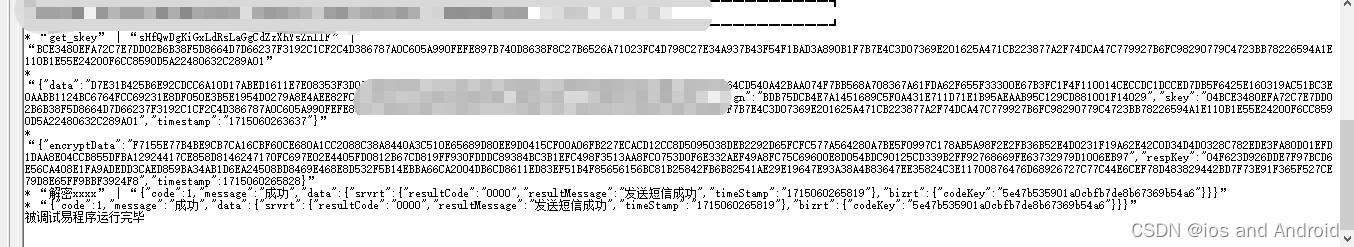
"*[GMSm* *]"3.抓包查看接口
例如:发送请求数据为
{"data":"D7E31B425B6E92CDCC6A10D17ABED1611E7E08353F3D07485CB899F7C15F79910040184F85F61D7DDD4486EAD694F81BE3780BC92064CD540A42BAA079","skey":"04BCE3480EFA72C7E7DD02B6B38F5D8664D7D66237F3192C1CF2C4D386787A0C605A990FEFE897B740D8638F8C27B6526A71023FC4D798C27E34A937B43F54F1BAD3A890B1F7B7E4C3D07369E201625A471CB223877A2F74DCA47C779927B6FC98290779C4723BB78226594A1E110B1E55E24200F6CC8590D5A22480632C289A01","timestamp":"1715060263637"}
{"
data":"D7E31B425B6E92CDCC6A10D17ABED1611E7E08353F3D07485CB899F7C15F79910040184F85F61D7DDD4486EAD694F81BE3780BC92064CD540A42BAA074F7BB568A708367A61FDA62F655F33300E67B3080A",
"sign":"BDB75DCB4E7A1451689C5F0A431E711D71E1B95AEAAB95C129CD881001F14029","
skey":"04BCE3480EFA72C7E7DD02B6B38F5D8664D7D66237F3192C1CF2C4D386787A0C605A990FEFE897B740D8638F8C27B6526A71023FC4D798C27E34A937B43F54F1BAD3A890B1F7B7E4C3D07369E201625A471CB223877A2F74DCA47C779927B6FC98290779C4723BB78226594A1E110B1E55E24200F6CC8590D5A22480632C289A01",
"timestamp":"1715060263637
"}
4.分析加密数据
字段有
data,sign,skey,timestamp
timestamp为:
当前时间戳
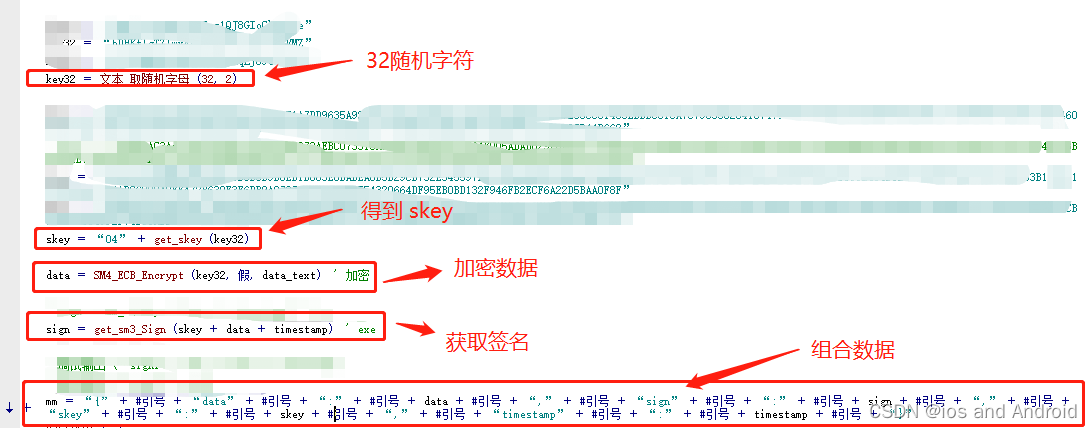
skey 的算法为:
sm2 加密 随机32位字符串,结果为skey
data 的算法为:
sm4 加密 发送的请问数据,密钥为: 上面随机32位字符串
sign 的算法为:
sm3 加密 (skey + data + timestamp)
5.易语言编写代码
计算加密:
运行结果: